Hybrid Identity Passwords-Describe security, compliance, privacy, and trust in Microsoft 365
Passwords in AD DS are stored as a hash (a one-way mathematical algorithm that cannot be reversed to extract the password), and by default, Azure AD Connect applies another hash algorithm to the AD DS hash. Thus, the password transmitted by Azure AD Connect to the cloud is secured by it being a hash of a hash. The passwords in Entra ID are never stored in plain text or encrypted using a reversible algorithm.
After the initial synchronization, Azure AD Connect continues to detect changes made to the AD DS identities and replicates those changes to the corresponding Entra ID identities in the cloud, as shown in Figure 3-8. Therefore, administrators managing hybrid identities must use the AD DS tools—such as Active Directory Users and Computers—to make changes to the on-premises user accounts. Because the identity replication flows in only one direction—from AD DS to Entra ID—no one should make changes directly to the cloud identities using the Microsoft 365 tools.
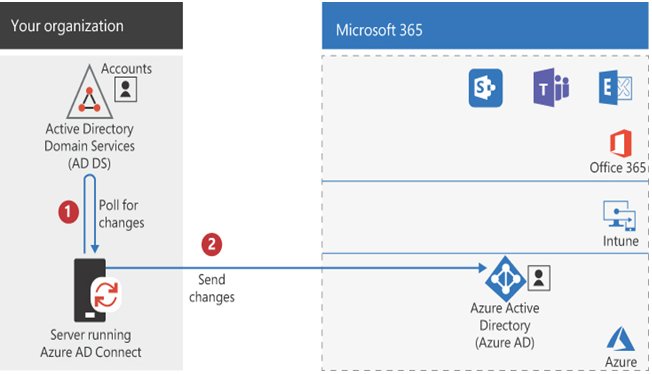
FIGURE 3-8 Azure AD Connect identity synchronization
Note Entra ID Application Proxy
While Entra ID is not a replacement for AD DS, it can provide remote users with access to internal web applications using a feature called Application Proxy. Application Proxy consists of a service that runs in the cloud and a connector that administrators install on an on-premises server. When remote clients attempt to access the internal web application with a URL, they are directed to an Entra ID sign-in page, where they authenticate using an Entra ID identity. The clients then pass the token they received as a result of the sign-in to the Application Proxy Service, which forwards it to the Application Proxy Connector on the internal network. The connector then forwards the user’s request to the internal web application, which returns its response to the client through the connector and the Application Proxy Service.
Hybrid identities can simplify the identity management process for administrators, but they can also simplify the user experience as well. For administrators adding cloud services to an existing on-premises infrastructure, the main objective should be to make user access to the cloud applications as invisible as possible. One way to do this is to implement single sign-on (SSO) so that users can authenticate with their familiar AD DS credentials and receive access to the cloud services without signing in again, either at the Entra ID level or in the individual applications. Another seamless single sign-on option enables users connected to the enterprise network to automatically sign in without any interactive authentication. Seamless sign-on is compatible with password hash synchronization and pass-through authentication methods but incompatible with the federated authentication method.
